Industrial Control System Security System Architecture and Management Platform
2019-02-07 22:05:05
Abstract: The "Stuxnet" virus that occurred in Iranian nuclear power plant in October 2010 sounded an alarm for the safety of industrial production control systems. At present, domestic and foreign production companies have put the construction of industrial control system safety protection on the agenda. Based on the analysis of the characteristics of the industrial control system and the security risks it faces, this paper proposes the architecture of the industrial control system security system, and explains the core product of the industrial control system, Sunstar's industrial control system security management platform.
First, industrial control system safety analysis Industrial control system (Industrial Control Systems, ICS), is composed of a variety of automatic control components and real-time data acquisition, monitoring process control components together. Its components include SCADA, Distributed Control System (DCS), Programmable Logic Controller (PLC), Remote Terminal (RTU), Intelligent Electronic Device (IED), and interface technology to ensure communication between components. .
The typical ICS control process is usually completed by three parts: control loop, HMI, and remote diagnosis and maintenance tool. The control loop is used to control logical operations. The HMI performs information exchange. The remote diagnosis and maintenance tools ensure that the ICS can run stably and continuously.
1.1 Potential Risks of Industrial Control Systems 1. Operating System Security Vulnerability Problems Due to the compatibility of industrial control software and operating system patches, the system will generally not patch the Windows platform after the system is started, causing the system to run with risks.
2. Anti-virus software installation and upgrade issues The Windows operating system used in production control systems is based on the consideration of compatibility between industrial control software and anti-virus software. Anti-virus software is usually not installed, leaving room for the spread and spread of viruses and malicious code.
3. The use of U disk, CD-ROM caused by the spread of the virus.
As the management terminal in the industrial control system generally does not have technical measures to effectively manage the use of the U disk and the optical disk, the security events caused by the disorderly use of the peripheral devices occur from time to time.
4. The casual accessibility of notebook computers during equipment maintenance The management and maintenance of industrial control systems. Laptops that do not reach a certain safety baseline are connected to the industrial control system and pose a great threat to the security of the industrial control system.
5. There is a risk that the industrial control system is intentionally or unintentionally controlled If there is no monitoring and response to the operating behavior of the industrial control system, abnormal behavior or human behavior in the industrial control system will bring great risks to the industrial control system.
6. Industrial control systems control terminals, servers, and network equipment failures without timely detection and response delays The monitoring of the operational status of IT infrastructure in industrial control systems is the basis for the stable operation of industrial industrial control systems.
1.2 "Industrialization and integration" risks to the industrial control system The industrial control system was isolated from the enterprise management system at the earliest, but in recent years, in order to achieve real-time data acquisition and production control, it meets the needs of "integration of two systems" and the convenience of management. Through logic isolation, the industrial control system and the enterprise management system can directly communicate. The enterprise management system is generally directly connected to the Internet. In this case, the scope of access of the industrial control system not only extends to the enterprise network, but also faces Threat from the Internet.
At the same time, in order to achieve the integration of management and control, the company has improved the level of integrated information automation, realized high efficiency and high efficiency in production and management, introduced the MES for production execution, and integrated industrial control systems and management information systems. Data exchange between the management information network and the production control network is realized. The result is that the production control system is no longer a stand-alone system, but must be interconnected and interconnected with the management system or even the Internet.
1.3 Industrial Control Systems Risks Caused by General-purpose Hardware and Software The industrial control system develops to the industrial Ethernet structure and becomes more and more open. OPC technology based on TCP/IP Ethernet communication has been widely used in this field. In industrial control systems, due to the ease of integration and use of industrial systems, a large number of industrial Ethernet ring networks and OPC communication protocols have been used for industrial control system integration; at the same time, a large number of PC servers and terminal products have also been used. And the database also uses a large number of general-purpose systems and is vulnerable to attacks from viruses, Trojans, and hackers from the corporate management network or the Internet.
Second, industrial control system security protection design Through the above analysis of the industrial control system security situation, we can see that the industrial control system uses a common platform to increase the security risks faced by the industrial control system, and "two integration" and the industrial control system itself The security risks caused by defects mainly come from two aspects of security protection.
Through the “three-tier architecture and two-tier protection†architecture, the industrial enterprise information system is layered, divided into domains, and graded, so that the operating behavior of the industrial control system is strictly and exclusively controlled to ensure the unique operation of the industrial control system. Sex.
Through the industrial control system security management platform, ensure that the HMI, the management machine, and the control service industrial control communication facilities are safe and credible.
2
2.1 Construction of a "three-tier architecture, two-tier protection" security system Industrial control systems need to be layered horizontally, vertically and horizontally, and regionally classified for security protection, otherwise management information systems, production execution systems, and industrial control systems are on the same network plane. The level is not clear, you have me, I have you. Intrusion or virus behavior from the management information system can easily damage the industrial control system. Network storms and denial-of-service attacks can easily consume system resources, making normal service functions impossible.
2.1.1 Three-tier structure of industrial control systems Information systems of general industrial enterprises can be divided into management, manufacturing execution, and industrial control. Between the management information layer and the manufacturing execution system layer, security protection such as identity authentication, access control, detection and auditing, link redundancy, and content detection is mainly performed; between the manufacturing execution system layer and the industrial control system layer, management is mainly avoided. The layer directly accesses the industrial control layer and guarantees the uniqueness of the manufacturing execution layer to the industrial control layer. The three-tier structure of the industrial control system is shown below: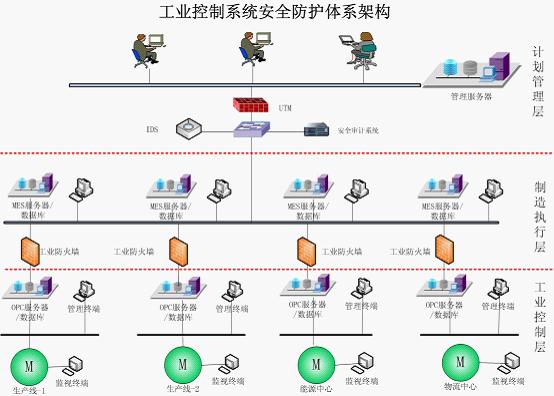
Through the above figure, we can see that the industrial enterprise information system is divided into three levels, namely the plan management layer, the manufacturing execution layer, and the industrial control layer.
Management system refers to the management information system (MIS) represented by ERP, which contains many subsystems, such as: production management, material management, financial management, quality management, workshop management, energy management, sales management, personnel management, equipment Management, technical management, comprehensive management, etc., management information system integrates information service and decision support.
The Manufacturing Execution System (MES) is located between the industrial control system and the management system and is mainly responsible for production management and scheduling execution. Through MES, managers can grasp and understand the changes in the operating conditions and process parameters of the various processes of the production process in time, and realize the process monitoring and control of the process.
The industrial control system is composed of various automatic control components and real-time data acquisition and monitoring process control components. Mainly complete the processing operations, testing and control operations, job management and other functions.
2.1.2 Layer 2 protection of industrial control systems 1. Security protection between management layer and MES layer Security protection between management layer and MES layer is mainly to avoid data exchange between management information system domain and MES (manufacturing execution) domain. Faced with various threats, the specific manifestations are: to avoid unauthorized access and abuse (such as business operators to operate other business systems beyond their authority); to operational errors, tamper data, repudiation can be controlled, traceable; to avoid terminal violations; timely Discovery of illegal intrusions; filtering of malicious code (virus worms).
In other words, the security protection between the management layer and the MES layer ensures that only trusted and compliant terminals and servers can perform secure data exchange between the two regions. At the same time, the whole process of data exchange is monitored and audited. . The security protection between the management layer and the MES layer is shown below: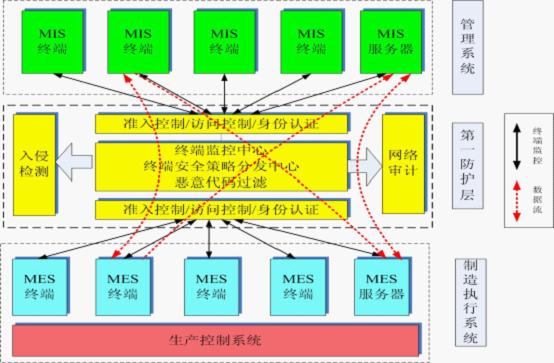
2. Security protection between MES layer and industrial control layer By deploying an industrial firewall at the MES layer and production control layer, it is possible to prevent the spread of viruses from the enterprise information layer; to block illegal intrusion from the enterprise information layer; to control the OPC client and server. The newsletter achieves the following goals:
Regional isolation and communication control: Through the industrial firewall filtering the communication between the two regional networks of the MES layer and the production control layer, the network failure will be controlled in the initial area, without affecting other parts.
Real-time alarm: Any illegal access to the real-time alarm information generated by the management platform, so that the fault problem will be quickly found and resolved in the original area.
The security protection between the MES layer and the industrial control layer is shown below:
2.1.3 Security Protection of Industrial Control Systems Domain security domains are subnets or networks that share the same security protection requirements, trust each other, and have the same security access control and border control policies, and share the same network security domain. The same security policy.
In the management layer, manufacturing execution layer, and industrial control layer, the security system subdivision of the management system is divided, the division of the manufacturing execution security sub-domain, and the division of the industrial control security sub-domain are performed. The rational division of security domains requires the use of a clear boundary for each security domain to facilitate the security protection of security domains. The security domain of MES and ICS is divided as shown below: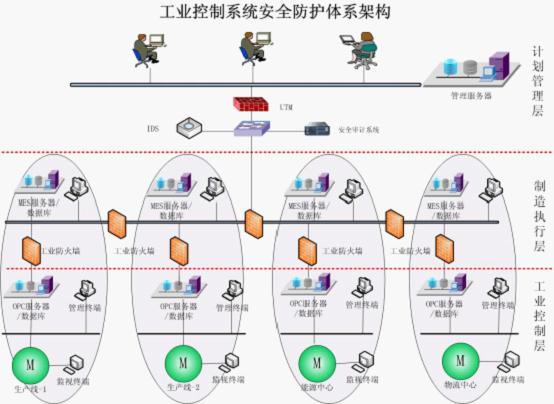
As shown in the above figure, in order to ensure the safety of various production lines, security zones are divided for each production line, and security isolation protection is performed between security zones.
2.1.4 Security classification of industrial control systems According to the importance of security domains in information systems and factors such as risk threats, security requirements, and security costs, they are classified into different levels of security protection and corresponding security protection technologies and management are adopted. Measures to safeguard information security.
The classification of security domains requires that the value of information assets in each security domain be similar, with the same or similar security levels, security environment, and security policies. The higher the value of the applications and assets involved in the security domain, the greater the threat they face, and the higher the level of security protection.
2.2 Building industrial control systems Safety management platforms Industrial control systems and traditional information systems have most of the same security issues, but they also have unique security requirements. The greatest safety requirements for industrial control systems are uniqueness and exclusivity. In a particular industrial control system, industrial control systems need only be run with unique industrial applications and industrial communication protocols. The others are not required.
VenusStar's industrial system security management platform has established a relatively credible computing environment for industrial control systems and has a very strong security control function for industrial control system management terminals and network communications. The industrial control system security management platform consists of two parts, one is the industrial control system security management platform, with terminal management, network management, and behavior monitoring functions, and the other is the terminal security management client.
2.2.1 Management platform The safe operation of some industrial control systems mainly needs to guarantee the security of the related information system infrastructure of industrial control systems, including industrial Ethernet networks, operating terminals, relational database servers, real-time database servers, operation and application systems, etc. The security of IT resources, from the perspective of industrial control system security, monitors various IT resources of the industrial control system (including equipment monitoring, operation monitoring and security monitoring), realizes early warning and response to security events, and ensures the safety of industrial control systems. Stable operation.
Specifically, the functions of the industrial control system security management platform are as follows:
1. Ability to monitor the operating status of application servers, relational database servers, real-time database servers, and industrial Ethernet devices, such as CPU, memory, port traffic, and more.
2. Ability to manage online and offline compliance of operating terminal peripherals, processes, and desktops.
3. Ability to monitor the boundary data exchange at each layer.
4. Ability to audit network operations in industrial control systems.
5. Ability to correlate and audit industrial control system logs.
6. Can provide early warning response to abnormal events in industrial control systems.
7. Ability to divide virtual security domains of industrial enterprise information systems.
2.2.2 Terminal security management of industrial control systems As the technical measures for security protection of industrial control system management terminals are very weak, attacks such as viruses, Trojans, and hackers exploit these security vulnerabilities, occur, initiate, and infect through the Internet. Or destroy other systems.
The most important feature of industrial control system terminals is the relatively fixed application. The terminal mainly installs industrial control system programs. Therefore, the most direct way to prevent malware such as viruses or Trojans in the traditional way is to use industrial control systems to manage the process of terminal application programs. .
Specifically, the terminal security management function of the industrial control system security management platform is as follows:
1. The industrial control system security management platform client software is light and refined, occupies few resources, and can ensure the stability of the industrial control system management terminal to the greatest degree.
2. The industrial control system security management platform client has a terminal access control function, which can prevent the notebook that has not reached the security baseline from managing the terminal.
3. The industrial control system security management platform client has terminal security optimization and reinforcement functions, and can optimize and reinforce the industrial control system terminal to ensure the terminal security level reaches a certain security baseline.
4. Industrial Control System Security Management Platform The client has peripheral management functions to manage the peripherals of industrial control systems, such as USB interface, optical drive, network card, and serial port.
5. The industrial control system security management platform client has the industrial control system application program monitoring function, and monitors and manages the industrial control system software in the terminal.
6. The industrial control system security management platform client has the industrial communication protocol monitoring function. The industrial control system terminal communication protocol is relatively fixed, and the client can have a unique management function for the terminal communication protocol.
7. The industrial control system security management platform client has an offline management function. Some industrial control system terminals cannot be managed online. The client has a relatively strong offline self-management function and can complete the management of offline terminals.
8. Industrial Control System The security management platform client has a strong identity authentication function, and the client has the use of an industrial control system. The online terminal and the offline terminal all have a strong identity authentication function, thereby preventing the risk that the industrial control system is intentionally or unintentionally controlled.
3. Conclusions There have been many production safety incidents caused by industrial control system safety problems at home and abroad. The most vivid example is the "Stuxnet" virus that occurred in Iran's Bushehr Nuclear Power Plant in October 2010, sounding the alarm for rectifying industrial production control systems.
To this end, the Ministry of Industry and Information Technology issued the “Circular on Strengthening the Information Security Management of Industrial Control Systems†in October 2011, requiring all levels of governments and large state-owned enterprises to effectively strengthen the safety management of industrial control systems. The Director of the Ministry of Industry and Information Technology, Zhao Zeliang, also stressed that the safety of industrial control systems is also time to be strengthened, otherwise it will affect the safety of China's important production facilities.
Based on the characteristics of industrial control system security protection, this paper proposes to layer, divide, and grade the industrial control system, and construct the "three-tier architecture, two-tier protection" industrial control system security system architecture ideas; through the analysis of industrial control systems The risks faced are described as the function of the safety management platform of the industrial control system, which is the core product of industrial control system safety protection. The industrial control system safety management platform is not only the product that realizes the terminal safety of the industrial control system, but also the platform that monitors the IT implementation and operation behavior of the industrial control system.
First, industrial control system safety analysis Industrial control system (Industrial Control Systems, ICS), is composed of a variety of automatic control components and real-time data acquisition, monitoring process control components together. Its components include SCADA, Distributed Control System (DCS), Programmable Logic Controller (PLC), Remote Terminal (RTU), Intelligent Electronic Device (IED), and interface technology to ensure communication between components. .
The typical ICS control process is usually completed by three parts: control loop, HMI, and remote diagnosis and maintenance tool. The control loop is used to control logical operations. The HMI performs information exchange. The remote diagnosis and maintenance tools ensure that the ICS can run stably and continuously.
1.1 Potential Risks of Industrial Control Systems 1. Operating System Security Vulnerability Problems Due to the compatibility of industrial control software and operating system patches, the system will generally not patch the Windows platform after the system is started, causing the system to run with risks.
2. Anti-virus software installation and upgrade issues The Windows operating system used in production control systems is based on the consideration of compatibility between industrial control software and anti-virus software. Anti-virus software is usually not installed, leaving room for the spread and spread of viruses and malicious code.
3. The use of U disk, CD-ROM caused by the spread of the virus.
As the management terminal in the industrial control system generally does not have technical measures to effectively manage the use of the U disk and the optical disk, the security events caused by the disorderly use of the peripheral devices occur from time to time.
4. The casual accessibility of notebook computers during equipment maintenance The management and maintenance of industrial control systems. Laptops that do not reach a certain safety baseline are connected to the industrial control system and pose a great threat to the security of the industrial control system.
5. There is a risk that the industrial control system is intentionally or unintentionally controlled If there is no monitoring and response to the operating behavior of the industrial control system, abnormal behavior or human behavior in the industrial control system will bring great risks to the industrial control system.
6. Industrial control systems control terminals, servers, and network equipment failures without timely detection and response delays The monitoring of the operational status of IT infrastructure in industrial control systems is the basis for the stable operation of industrial industrial control systems.
1.2 "Industrialization and integration" risks to the industrial control system The industrial control system was isolated from the enterprise management system at the earliest, but in recent years, in order to achieve real-time data acquisition and production control, it meets the needs of "integration of two systems" and the convenience of management. Through logic isolation, the industrial control system and the enterprise management system can directly communicate. The enterprise management system is generally directly connected to the Internet. In this case, the scope of access of the industrial control system not only extends to the enterprise network, but also faces Threat from the Internet.
At the same time, in order to achieve the integration of management and control, the company has improved the level of integrated information automation, realized high efficiency and high efficiency in production and management, introduced the MES for production execution, and integrated industrial control systems and management information systems. Data exchange between the management information network and the production control network is realized. The result is that the production control system is no longer a stand-alone system, but must be interconnected and interconnected with the management system or even the Internet.
1.3 Industrial Control Systems Risks Caused by General-purpose Hardware and Software The industrial control system develops to the industrial Ethernet structure and becomes more and more open. OPC technology based on TCP/IP Ethernet communication has been widely used in this field. In industrial control systems, due to the ease of integration and use of industrial systems, a large number of industrial Ethernet ring networks and OPC communication protocols have been used for industrial control system integration; at the same time, a large number of PC servers and terminal products have also been used. And the database also uses a large number of general-purpose systems and is vulnerable to attacks from viruses, Trojans, and hackers from the corporate management network or the Internet.
Second, industrial control system security protection design Through the above analysis of the industrial control system security situation, we can see that the industrial control system uses a common platform to increase the security risks faced by the industrial control system, and "two integration" and the industrial control system itself The security risks caused by defects mainly come from two aspects of security protection.
Through the “three-tier architecture and two-tier protection†architecture, the industrial enterprise information system is layered, divided into domains, and graded, so that the operating behavior of the industrial control system is strictly and exclusively controlled to ensure the unique operation of the industrial control system. Sex.
Through the industrial control system security management platform, ensure that the HMI, the management machine, and the control service industrial control communication facilities are safe and credible.
2
2.1 Construction of a "three-tier architecture, two-tier protection" security system Industrial control systems need to be layered horizontally, vertically and horizontally, and regionally classified for security protection, otherwise management information systems, production execution systems, and industrial control systems are on the same network plane. The level is not clear, you have me, I have you. Intrusion or virus behavior from the management information system can easily damage the industrial control system. Network storms and denial-of-service attacks can easily consume system resources, making normal service functions impossible.
2.1.1 Three-tier structure of industrial control systems Information systems of general industrial enterprises can be divided into management, manufacturing execution, and industrial control. Between the management information layer and the manufacturing execution system layer, security protection such as identity authentication, access control, detection and auditing, link redundancy, and content detection is mainly performed; between the manufacturing execution system layer and the industrial control system layer, management is mainly avoided. The layer directly accesses the industrial control layer and guarantees the uniqueness of the manufacturing execution layer to the industrial control layer. The three-tier structure of the industrial control system is shown below:

Through the above figure, we can see that the industrial enterprise information system is divided into three levels, namely the plan management layer, the manufacturing execution layer, and the industrial control layer.
Management system refers to the management information system (MIS) represented by ERP, which contains many subsystems, such as: production management, material management, financial management, quality management, workshop management, energy management, sales management, personnel management, equipment Management, technical management, comprehensive management, etc., management information system integrates information service and decision support.
The Manufacturing Execution System (MES) is located between the industrial control system and the management system and is mainly responsible for production management and scheduling execution. Through MES, managers can grasp and understand the changes in the operating conditions and process parameters of the various processes of the production process in time, and realize the process monitoring and control of the process.
The industrial control system is composed of various automatic control components and real-time data acquisition and monitoring process control components. Mainly complete the processing operations, testing and control operations, job management and other functions.
2.1.2 Layer 2 protection of industrial control systems 1. Security protection between management layer and MES layer Security protection between management layer and MES layer is mainly to avoid data exchange between management information system domain and MES (manufacturing execution) domain. Faced with various threats, the specific manifestations are: to avoid unauthorized access and abuse (such as business operators to operate other business systems beyond their authority); to operational errors, tamper data, repudiation can be controlled, traceable; to avoid terminal violations; timely Discovery of illegal intrusions; filtering of malicious code (virus worms).
In other words, the security protection between the management layer and the MES layer ensures that only trusted and compliant terminals and servers can perform secure data exchange between the two regions. At the same time, the whole process of data exchange is monitored and audited. . The security protection between the management layer and the MES layer is shown below:

2. Security protection between MES layer and industrial control layer By deploying an industrial firewall at the MES layer and production control layer, it is possible to prevent the spread of viruses from the enterprise information layer; to block illegal intrusion from the enterprise information layer; to control the OPC client and server. The newsletter achieves the following goals:
Regional isolation and communication control: Through the industrial firewall filtering the communication between the two regional networks of the MES layer and the production control layer, the network failure will be controlled in the initial area, without affecting other parts.
Real-time alarm: Any illegal access to the real-time alarm information generated by the management platform, so that the fault problem will be quickly found and resolved in the original area.
The security protection between the MES layer and the industrial control layer is shown below:

2.1.3 Security Protection of Industrial Control Systems Domain security domains are subnets or networks that share the same security protection requirements, trust each other, and have the same security access control and border control policies, and share the same network security domain. The same security policy.
In the management layer, manufacturing execution layer, and industrial control layer, the security system subdivision of the management system is divided, the division of the manufacturing execution security sub-domain, and the division of the industrial control security sub-domain are performed. The rational division of security domains requires the use of a clear boundary for each security domain to facilitate the security protection of security domains. The security domain of MES and ICS is divided as shown below:

As shown in the above figure, in order to ensure the safety of various production lines, security zones are divided for each production line, and security isolation protection is performed between security zones.
2.1.4 Security classification of industrial control systems According to the importance of security domains in information systems and factors such as risk threats, security requirements, and security costs, they are classified into different levels of security protection and corresponding security protection technologies and management are adopted. Measures to safeguard information security.
The classification of security domains requires that the value of information assets in each security domain be similar, with the same or similar security levels, security environment, and security policies. The higher the value of the applications and assets involved in the security domain, the greater the threat they face, and the higher the level of security protection.
2.2 Building industrial control systems Safety management platforms Industrial control systems and traditional information systems have most of the same security issues, but they also have unique security requirements. The greatest safety requirements for industrial control systems are uniqueness and exclusivity. In a particular industrial control system, industrial control systems need only be run with unique industrial applications and industrial communication protocols. The others are not required.
VenusStar's industrial system security management platform has established a relatively credible computing environment for industrial control systems and has a very strong security control function for industrial control system management terminals and network communications. The industrial control system security management platform consists of two parts, one is the industrial control system security management platform, with terminal management, network management, and behavior monitoring functions, and the other is the terminal security management client.
2.2.1 Management platform The safe operation of some industrial control systems mainly needs to guarantee the security of the related information system infrastructure of industrial control systems, including industrial Ethernet networks, operating terminals, relational database servers, real-time database servers, operation and application systems, etc. The security of IT resources, from the perspective of industrial control system security, monitors various IT resources of the industrial control system (including equipment monitoring, operation monitoring and security monitoring), realizes early warning and response to security events, and ensures the safety of industrial control systems. Stable operation.
Specifically, the functions of the industrial control system security management platform are as follows:
1. Ability to monitor the operating status of application servers, relational database servers, real-time database servers, and industrial Ethernet devices, such as CPU, memory, port traffic, and more.
2. Ability to manage online and offline compliance of operating terminal peripherals, processes, and desktops.
3. Ability to monitor the boundary data exchange at each layer.
4. Ability to audit network operations in industrial control systems.
5. Ability to correlate and audit industrial control system logs.
6. Can provide early warning response to abnormal events in industrial control systems.
7. Ability to divide virtual security domains of industrial enterprise information systems.
2.2.2 Terminal security management of industrial control systems As the technical measures for security protection of industrial control system management terminals are very weak, attacks such as viruses, Trojans, and hackers exploit these security vulnerabilities, occur, initiate, and infect through the Internet. Or destroy other systems.
The most important feature of industrial control system terminals is the relatively fixed application. The terminal mainly installs industrial control system programs. Therefore, the most direct way to prevent malware such as viruses or Trojans in the traditional way is to use industrial control systems to manage the process of terminal application programs. .
Specifically, the terminal security management function of the industrial control system security management platform is as follows:
1. The industrial control system security management platform client software is light and refined, occupies few resources, and can ensure the stability of the industrial control system management terminal to the greatest degree.
2. The industrial control system security management platform client has a terminal access control function, which can prevent the notebook that has not reached the security baseline from managing the terminal.
3. The industrial control system security management platform client has terminal security optimization and reinforcement functions, and can optimize and reinforce the industrial control system terminal to ensure the terminal security level reaches a certain security baseline.
4. Industrial Control System Security Management Platform The client has peripheral management functions to manage the peripherals of industrial control systems, such as USB interface, optical drive, network card, and serial port.
5. The industrial control system security management platform client has the industrial control system application program monitoring function, and monitors and manages the industrial control system software in the terminal.
6. The industrial control system security management platform client has the industrial communication protocol monitoring function. The industrial control system terminal communication protocol is relatively fixed, and the client can have a unique management function for the terminal communication protocol.
7. The industrial control system security management platform client has an offline management function. Some industrial control system terminals cannot be managed online. The client has a relatively strong offline self-management function and can complete the management of offline terminals.
8. Industrial Control System The security management platform client has a strong identity authentication function, and the client has the use of an industrial control system. The online terminal and the offline terminal all have a strong identity authentication function, thereby preventing the risk that the industrial control system is intentionally or unintentionally controlled.
3. Conclusions There have been many production safety incidents caused by industrial control system safety problems at home and abroad. The most vivid example is the "Stuxnet" virus that occurred in Iran's Bushehr Nuclear Power Plant in October 2010, sounding the alarm for rectifying industrial production control systems.
To this end, the Ministry of Industry and Information Technology issued the “Circular on Strengthening the Information Security Management of Industrial Control Systems†in October 2011, requiring all levels of governments and large state-owned enterprises to effectively strengthen the safety management of industrial control systems. The Director of the Ministry of Industry and Information Technology, Zhao Zeliang, also stressed that the safety of industrial control systems is also time to be strengthened, otherwise it will affect the safety of China's important production facilities.
Based on the characteristics of industrial control system security protection, this paper proposes to layer, divide, and grade the industrial control system, and construct the "three-tier architecture, two-tier protection" industrial control system security system architecture ideas; through the analysis of industrial control systems The risks faced are described as the function of the safety management platform of the industrial control system, which is the core product of industrial control system safety protection. The industrial control system safety management platform is not only the product that realizes the terminal safety of the industrial control system, but also the platform that monitors the IT implementation and operation behavior of the industrial control system.
Steel Floor Deck Roll Forming Machine
Floor Decking Machine,Floor Decking Roll Forming Machine,Floor Grinding Machine
Willing Technology Co., Ltd. , http://www.txrollformingmachine.com